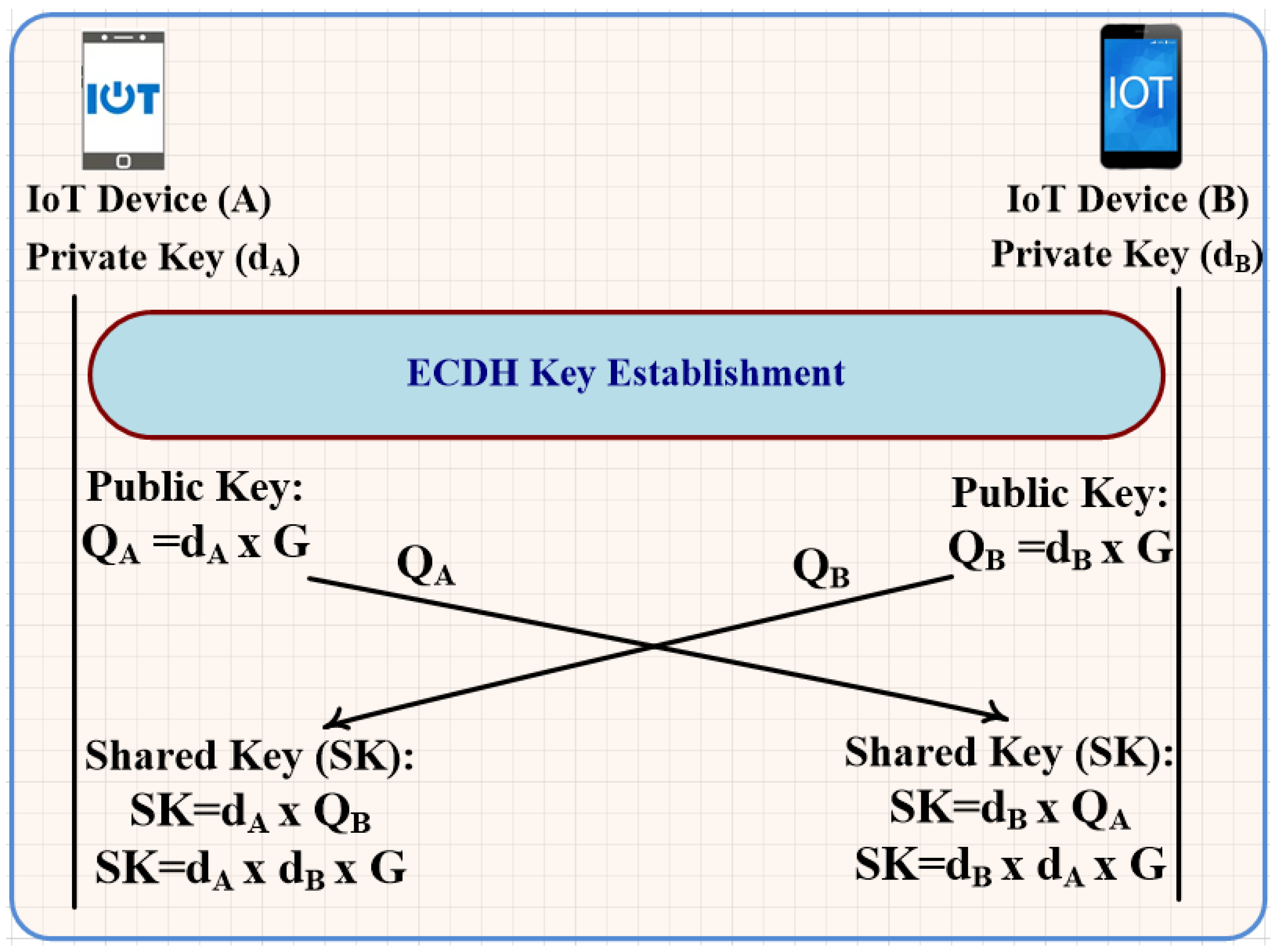
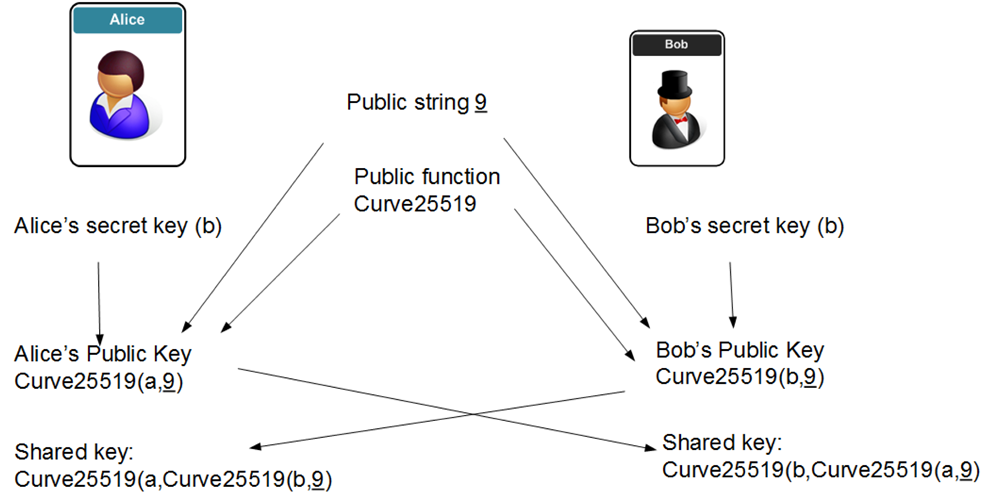
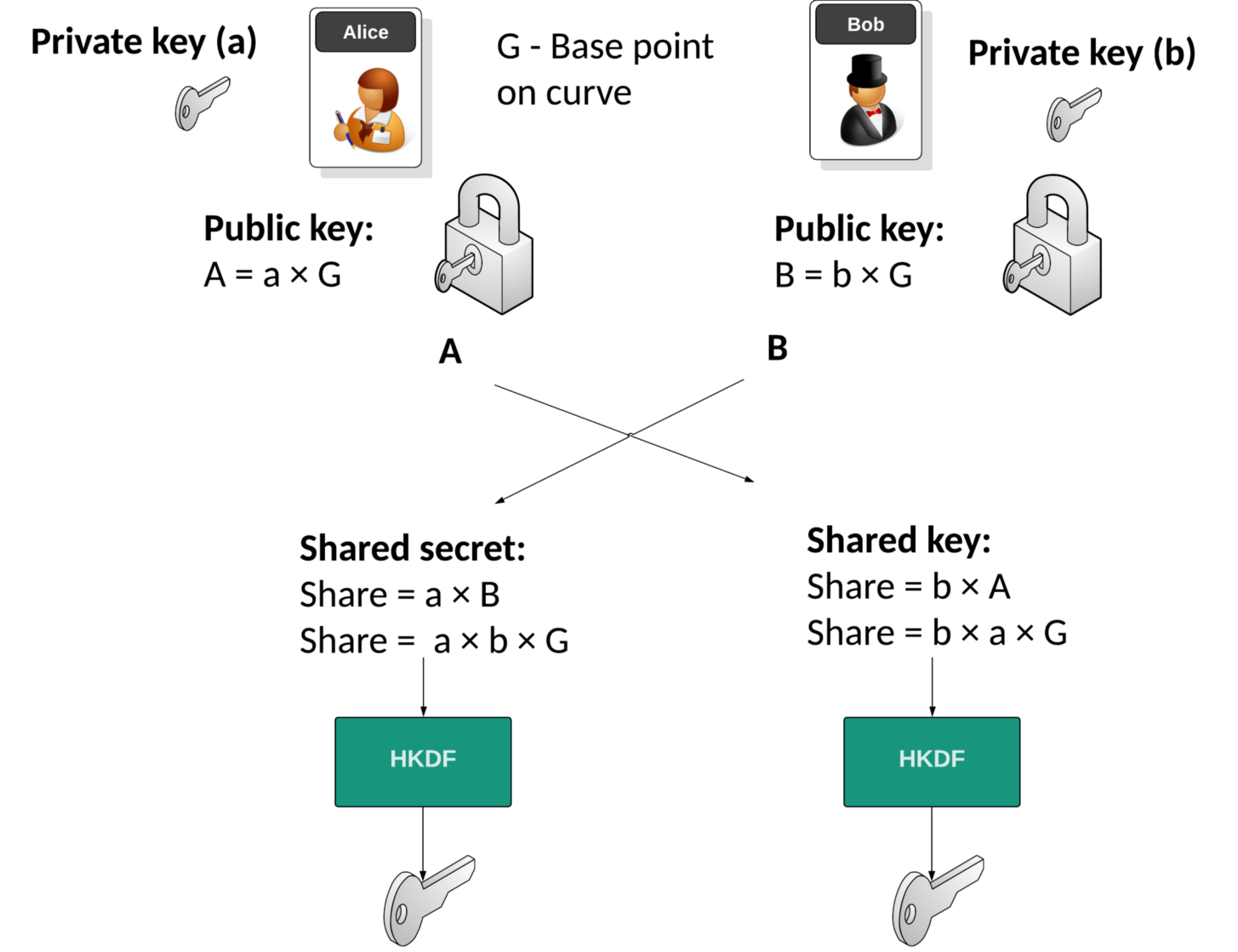
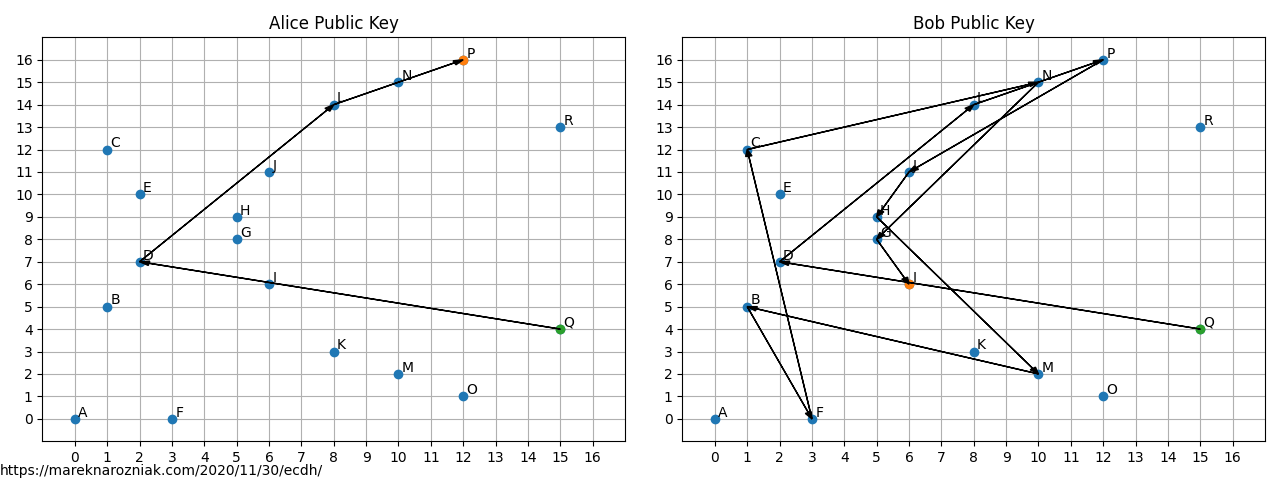
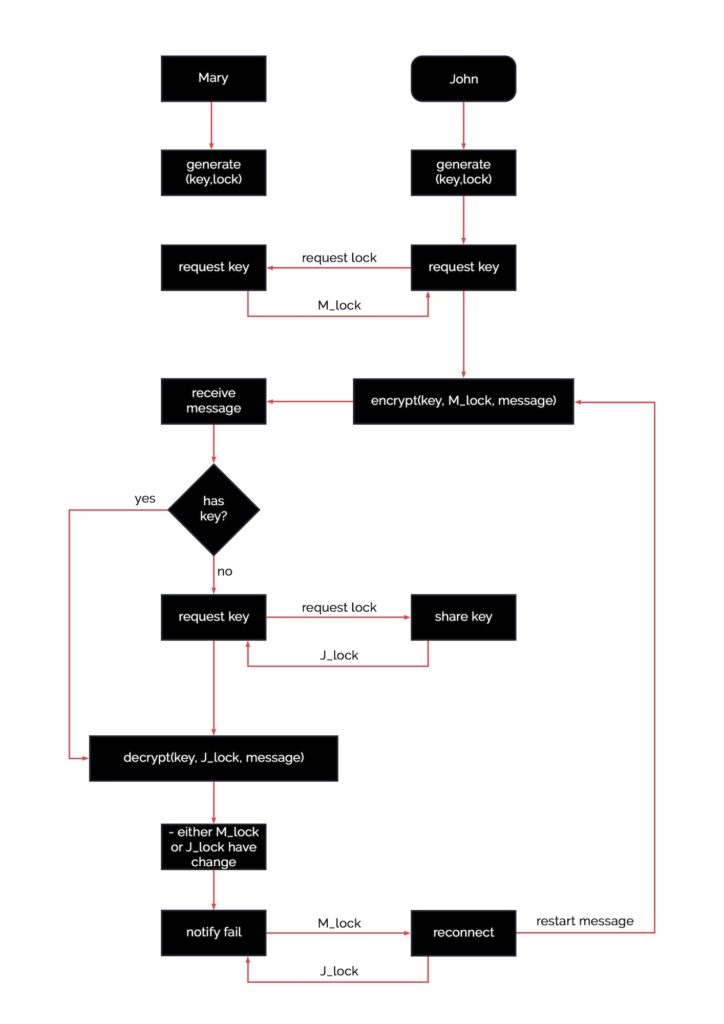
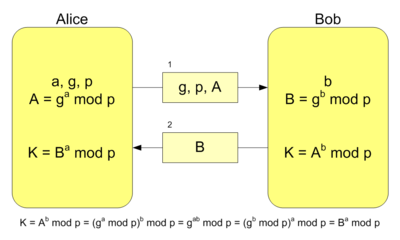
GitHub - elesiuta/ECDH: Elliptic-curve Diffie–Hellman key exchange in the binary finite field (GF(2^n))
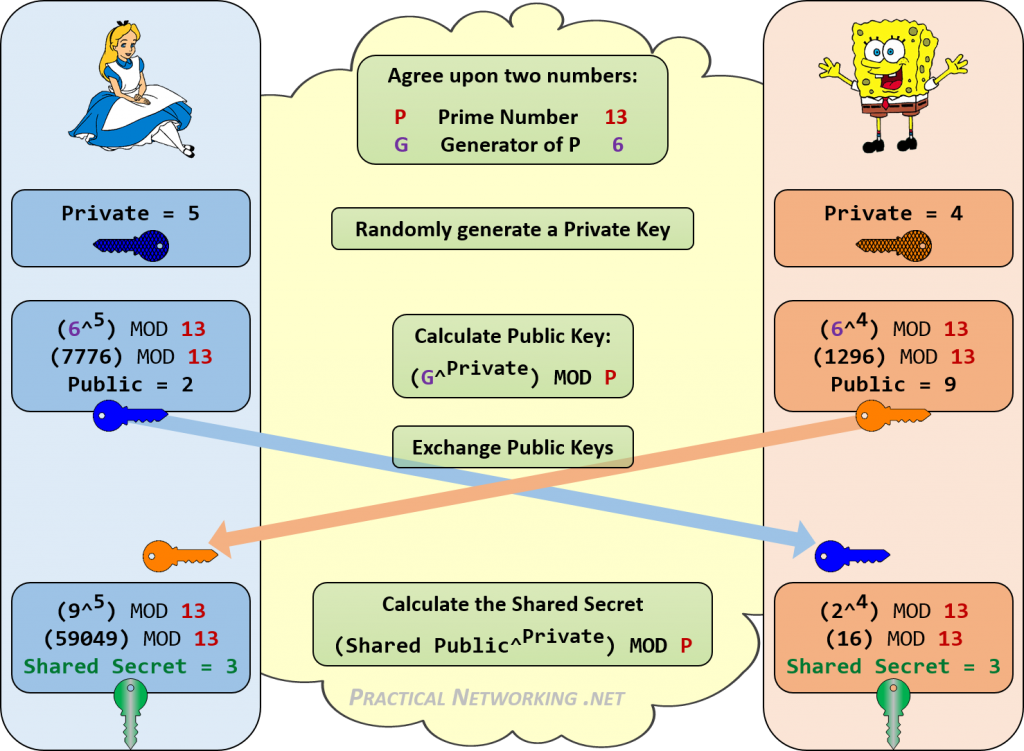
Implementing Elliptic-curve Diffie–Hellman Key Exchange Algorithm using C# (cross-platform) | David Tavarez

The Security Buddy on Twitter: "How does Elliptic Curve Cryptography work? https://t.co/f6k3Mbb0ls #security #encryption #ECDH https://t.co/z6uYu73g32" / Twitter
GitHub - jeswinMathai/SC-ECDH: Secure Communication System using Elleptic Curve Diffie Hellman Algorithm